Authors:
(1) Dong Jiang, School of Internet, Anhui University, National Engineering Research Center of Agro-Ecological Big Data Analysis and Application, Anhui University & [email protected];
(2) Zhen Yuan, School of Internet, Anhui University;
(3) Wen-xin Li, School of Internet, Anhui University;
(4) Liang-liang Lu, Key Laboratory of Optoelectronic Technology of Jiangsu Province, Nanjing Normal University, National Laboratory of Solid State Microstructures, Nanjing University, Nanjing & [email protected].
Table of Links
7. Comparison To Previous Works
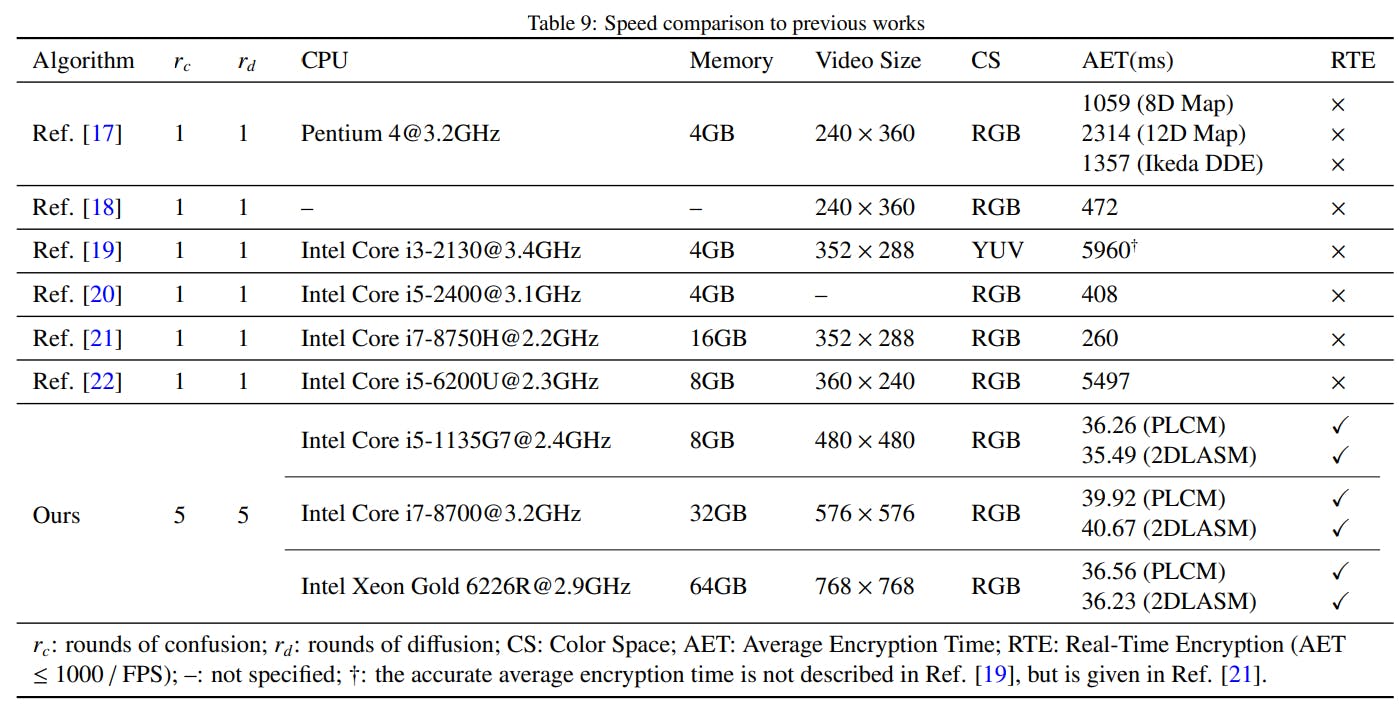
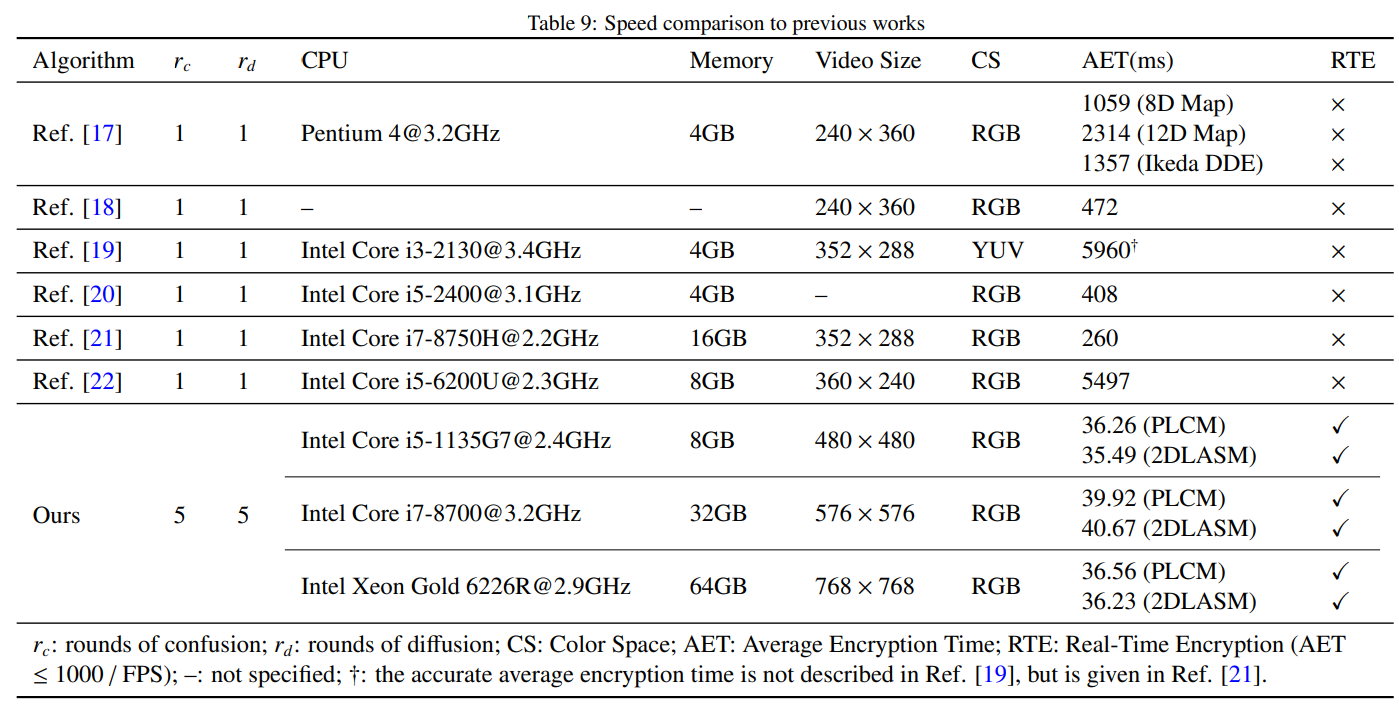
As discussed above, existing algorithms can be divided into full and selective video encryption. The proposed strategy, clearly, belongs to the former category. In this section, therefore, the deployed cryptosystems are compared with several recent published papers on full video encryption. The results are shown in Tab. 9. For some selected works, videos of different sizes are used to evaluate the encryption speed. We list the encryption speed for the largest videos in the table.
With the development of information science and hardware, the users put forward higher requirements for security. Thus almost all the latest works are based on confusion-diffusion architecture. To the best of our knowledge, however, these works only consist of one round of confusion and diffusion operation to improve the computational efficiency. And they cannot meet the requirements of real-time encryption, that is, the average encryption time (ms) of video frames is less than 1000 / FPS. Therefore, compare to previous works, the proposed strategy achieves the following advantages:
i) It realizes real-time video encryption, provides a feasible solution for related applications, and points out a new path for related research.
ii) By taking advantages of parallel computing technique, it proves that real-time video encryption based on multiround confusion-diffusion architecture is possible, and thus improves the security of real-time video encryption to the level of image encryption.
iii) It works with many confusion, diffusion methods, and different chaotic maps.
iv) It can be easily implemented with both software and hardware such as ARM, FPGA, etc.
This paper is available on arxiv under CC 4.0 license.